Certified Red Team Operator (CRTO) Course & Exam Review - 2025

29 May 2025 - Update - The course has been updated, including smaller and more objective based labs rather than one environment, updated coursework, and a new exam, with no cost for exam retakes AND lab time. I will be updating/rewriting this when I have completed the new coursework and exam. Also I did CRTL but that hasn't moved yet so I'll give a review of that after the course has updated and I've passed the exam.
Overview
Offered by Zero-Point Security, Red Team Operator is a course and certification aimed at beginner to intermediate (more-so intermediate) professionals in offensive security positions. It presents a challenging but fair environment for those interested in Red Teaming to practice with a Command & Control (C2) framework in exploiting an Active Directory environment.
Here, I'll be reviewing both the course and exam, sharing my experience with both and hoping to leave a bit of guidance to those looking for success themselves.
Coursework
At the time of writing the course is able to be purchased on its own, or with various tiers of lab time, which I feel are essential if you are going to attempt the exam as learning the ins and outs of Cobalt Strike will take a few hours at least if you're not already familiar. The course is a lifetime purchase and is consistently updated by the sole creator and maintainer of the course, Rasta-Mouse.
The course teaches you how to set up your C2, externally recon a target, compromise that target and move to a full domain takeover with persistence. Further to that you learn how to find data and exfiltrate it, as well as avoiding AV and EDR solutions (with the ability to check for the SIEM for alerts you may trigger). To say this is comprehensive does it a disservice, it covers a lot of ground regarding exploitable services you will find in an Active Directory domain from the perspective of using a C2 framework.
Presented in Snaplabs can sometimes make the content a little challenging to engage with, but it is certainly doable. You will not be able to import your own tools, export items, or use an alternative OS or C2 framework (Kali, Havoc, Sliver etc.). The most challenging aspect I found here was the latency with connecting from Australia, but it just took a little more patience.
Exam
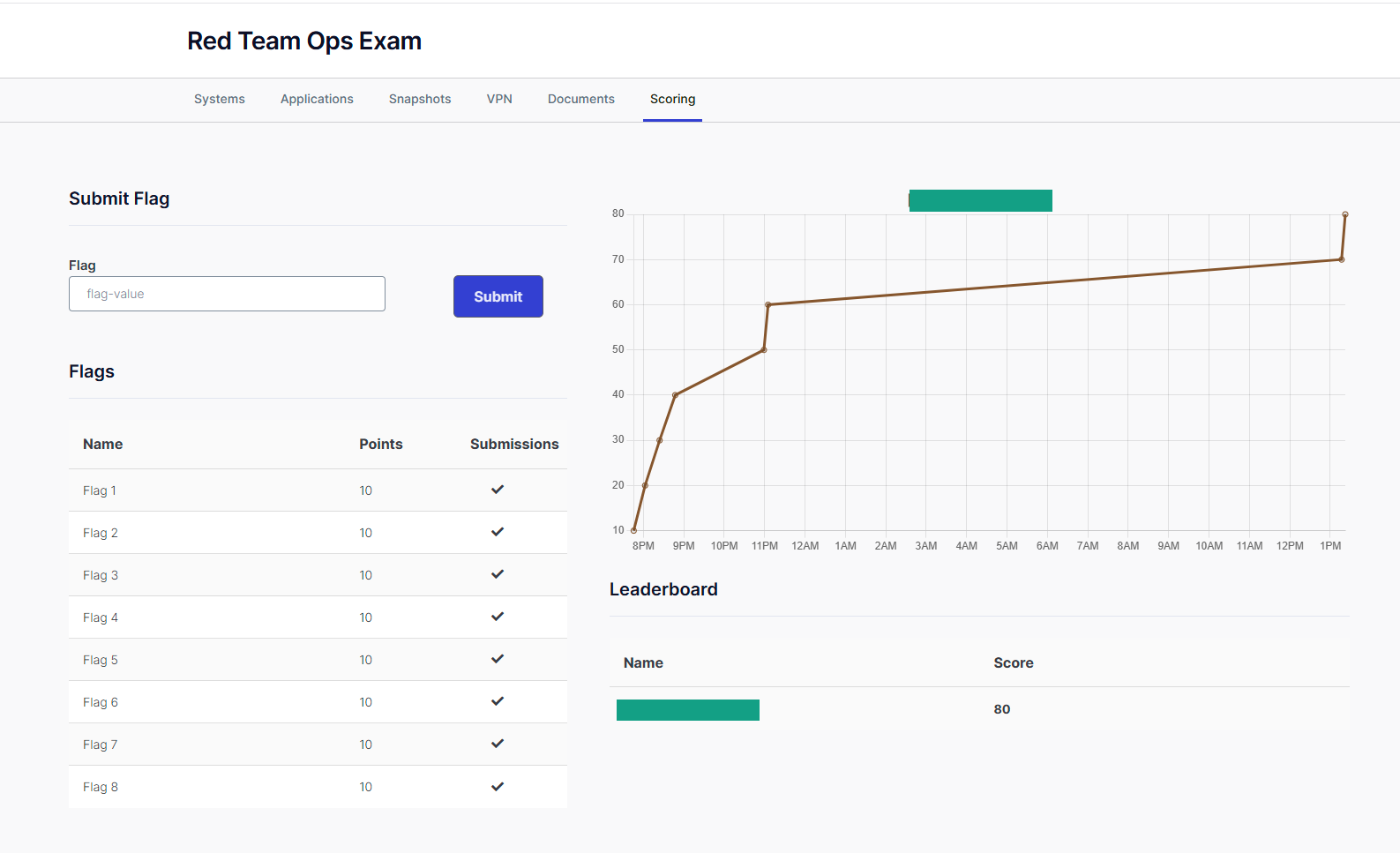
The exam is set with 48 hours of lab time to be used over 4 days, where labs can be stopped and started to save time during breaks and sleeping. There are 8 flags available, and 6 are required to pass, I found the main challenges to be at the 5th and 7th flags, which I believe is fair and fun to have one right before the home stretch and then another as a little bonus to make you feel all smart and good at hacking.
Establishing persistence is encouraged and in my opinion, mandatory, if you aren't practicing your persistence in the course labs, you're not going to be ready for this, and you'll lose time re-establishing beacons to the point you stopped prior. Another thing to practice and have ready is your modified artifact kit and c2 profile, it'll save you time and knowing it works before going in will have you just that little more confident, this can be achieved by running fully through the course lab with Defender turned on. The other main things you'll want to know, that you might have trouble with is identification of which Kerberos attacks to use & when, and pivoting; punching through a proxy is hard to visualise in your head but very rewarding when accomplished!
I found that the exam matched the course almost perfectly, everything I had to do in the exam was close to the coursework, with its own little flavour. Obviously the environment is different, and the coursework is so broad that not everything can be featured, but the essentials are covered well, with a little extra thrown in. The path to the 7th flag is definitely a little treat, and can be done in the practice lab but I felt was a little harder to pull off in the exam (most of the time between was sleeping I swear).
Tips
- Run through the lab once without Defender, and then at least once with Defender, this is MANDATORY!
- The tools you get given in the exam are a good hint for what's included, if the tool for an attack vector doesn't exist, you probably aren't supposed to use it.
- You do something and you lose your beacon? What's the easiest option? Maybe you have an alternative tool or method.
- If something isn't behaving as expected, and there's no alternatives, maybe somethings wrong with it?
- As you do the lab, draw out the network, this will help to understand how you can move around it, and pivot where required.
What Next?
And Maldev Academy 😄

